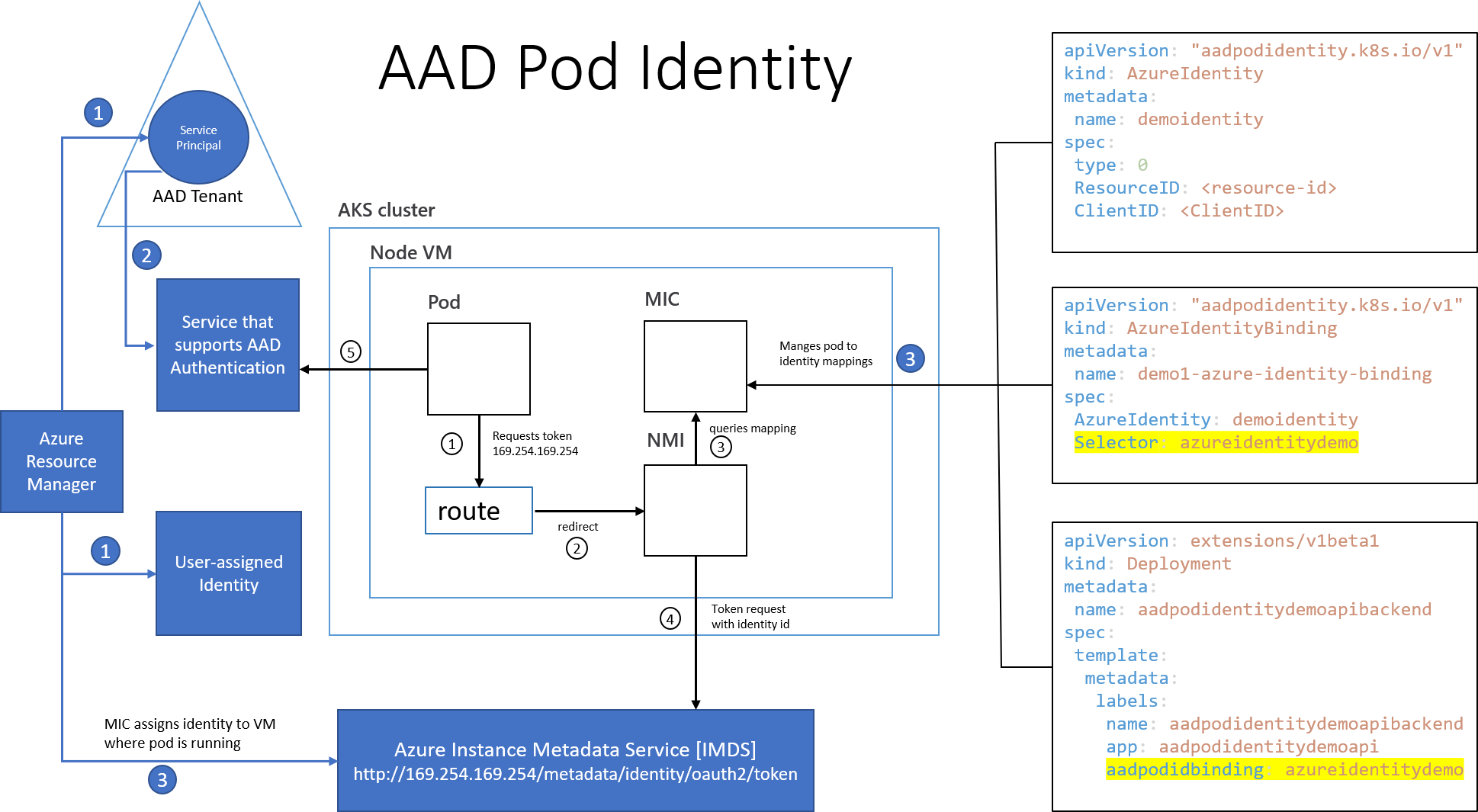
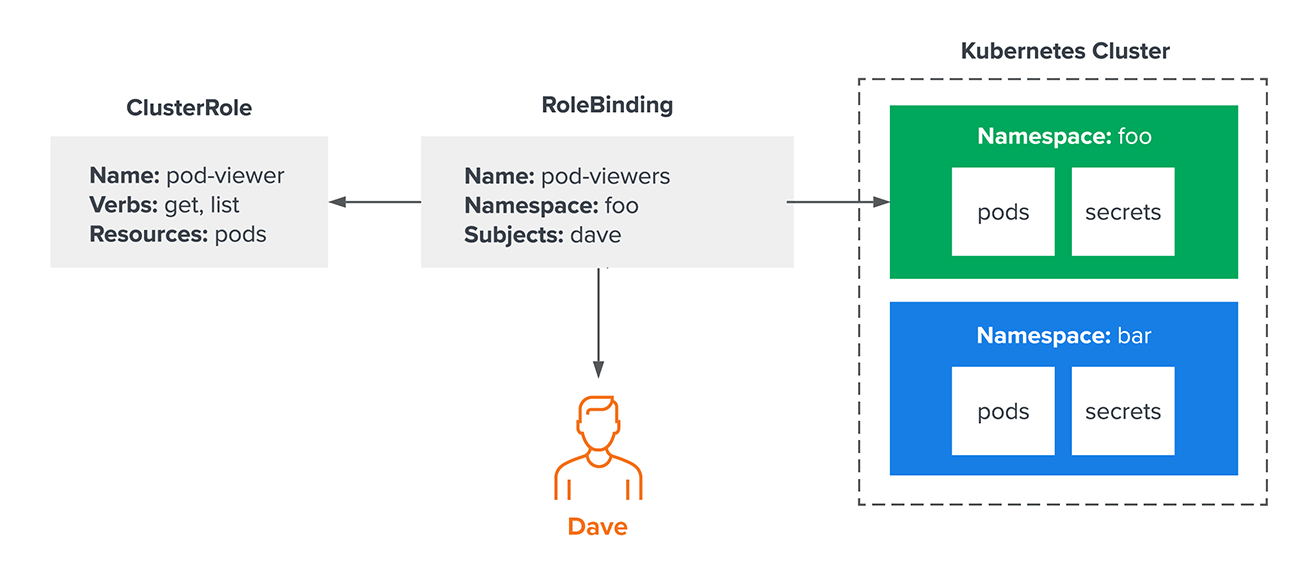
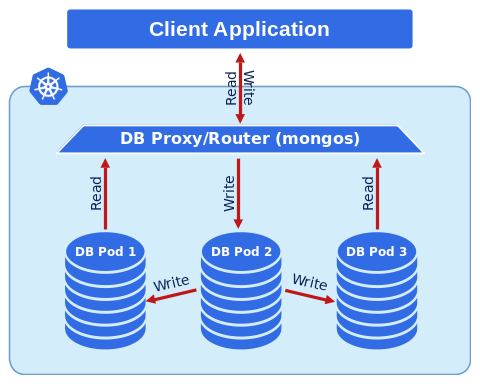
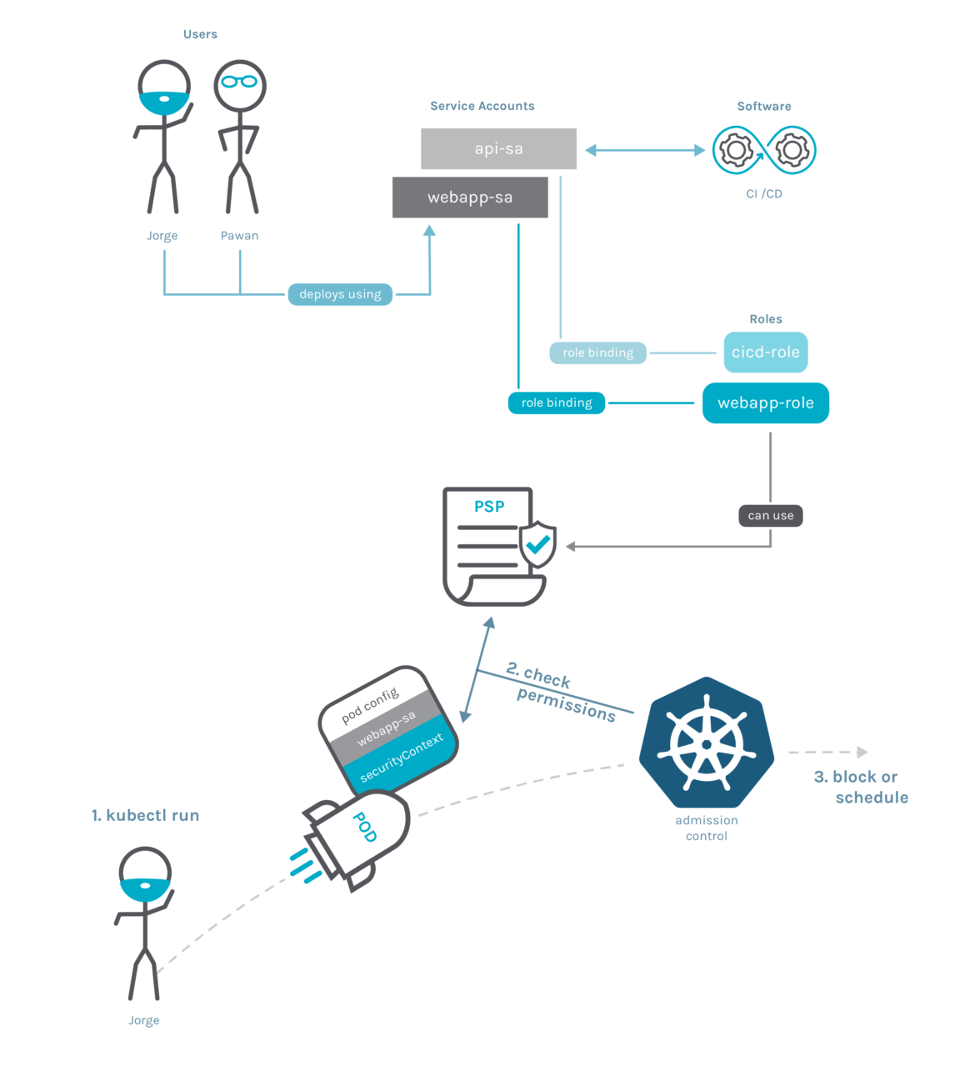
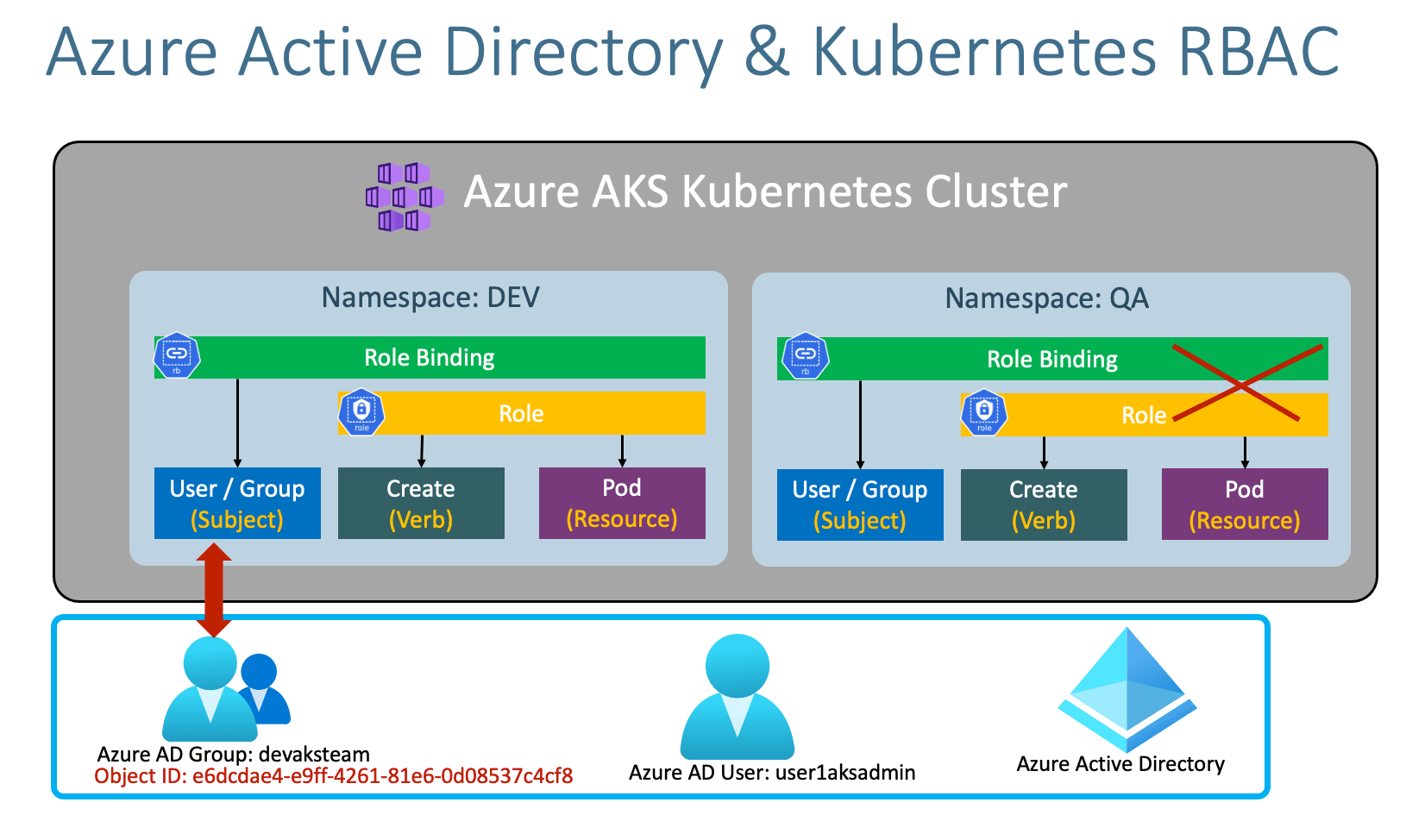
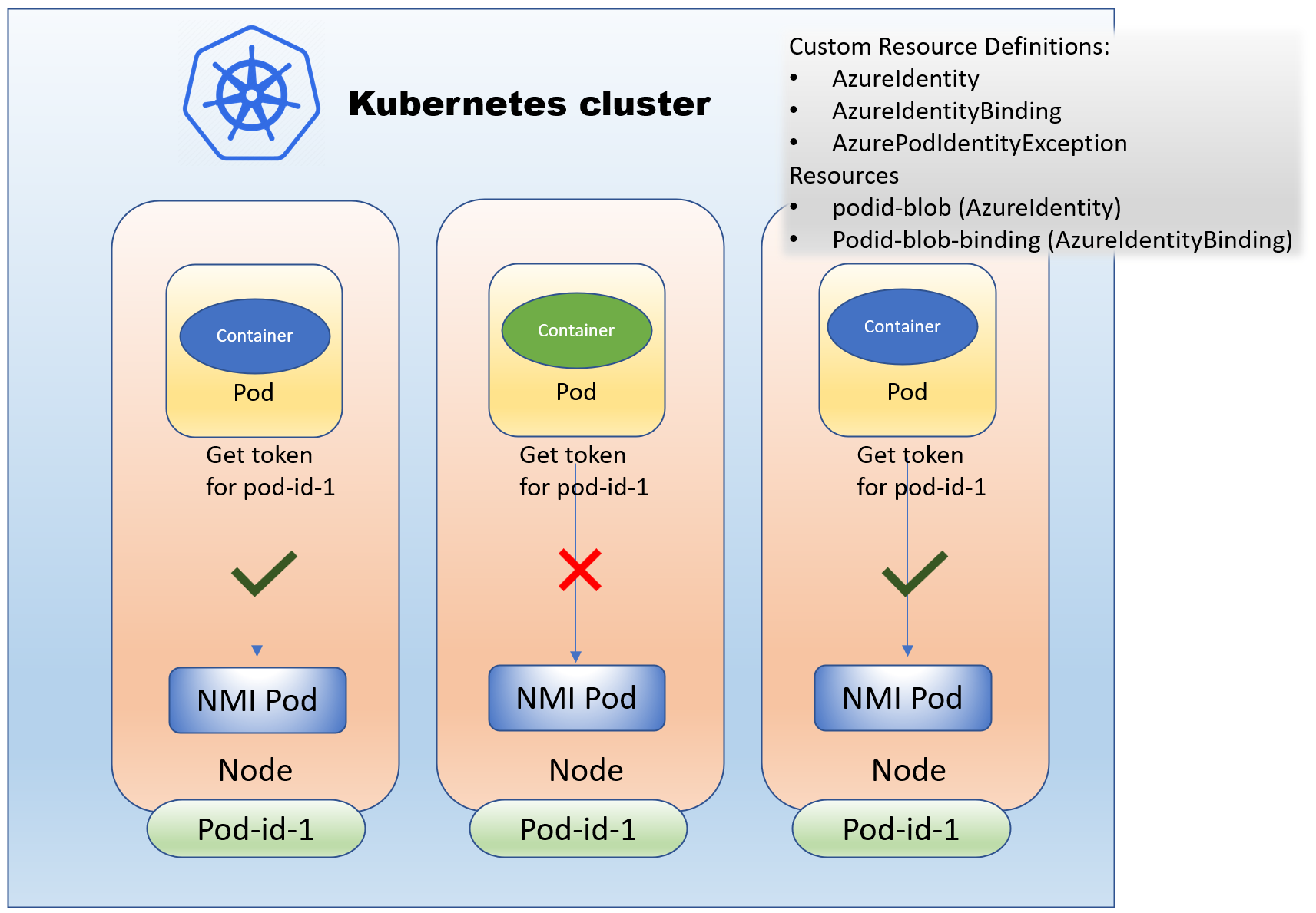
Using AAD Pod Identity in your Azure Kubernetes Clusters — what to watch out for! | by Paulo Gomes | ITNEXT

Managing Pod Scheduling Constraints and Groupless Node Upgrades with Karpenter in Amazon EKS | Containers

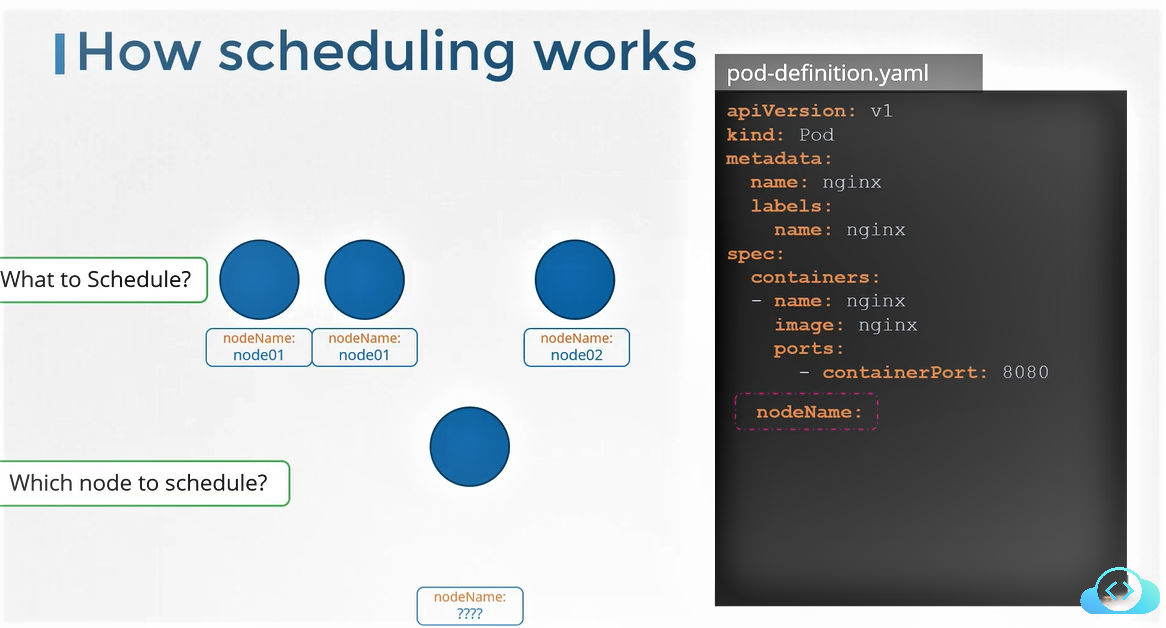
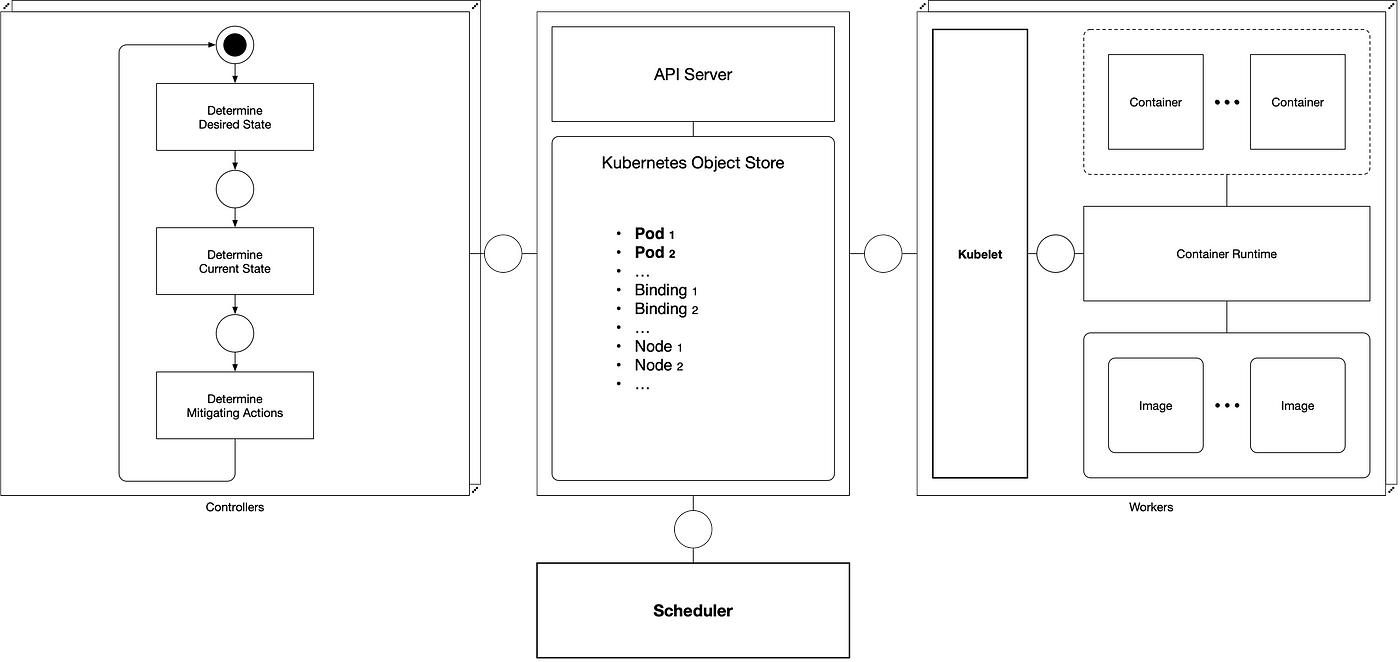
Getting Started with Kubernetes | Scheduling Process and Scheduler Algorithms - Alibaba Cloud Community

Getting Started with Kubernetes | Scheduling Process and Scheduler Algorithms - Alibaba Cloud Community